ESET Endpoint Antivirus for macOS 7 Bedienungsanleitung
- Typ
- Bedienungsanleitung

Copyright ©2023 by ESET, spol. s r.o.
ESET Endpoint Antivirus for macOS wurde entwickelt von ESET, spol. s r.o.
Weitere Informationen finden Sie unter https://www.eset.com.
Alle Rechte vorbehalten. Kein Teil dieser Dokumentation darf ohne schriftliche Einwilligung des Verfassers
reproduziert, in einem Abrufsystem gespeichert oder in irgendeiner Form oder auf irgendeine Weise
weitergegeben werden, sei es elektronisch, mechanisch, durch Fotokopien, Aufnehmen, Scannen oder auf andere
Art.
ESET, spol. s r.o. behält sich das Recht vor, ohne vorherige Ankündigung Änderungen an allen hier beschriebenen
Software-Anwendungen vorzunehmen.
Technischer Support: https://support.eset.com
REV. 28.09.2023

1 ESET Endpoint Antivirus for macOS 1 ..................................................................................................
2 Neuerungen in Version 7 1 ...................................................................................................................
2.1 Vergleich zwischen den Version 6 und 7 2 ........................................................................................
2.2 Einstellungen migrieren 6 ..............................................................................................................
2.3 Änderungslog 7 .............................................................................................................................
3 Systemanforderungen 7 .......................................................................................................................
4 Upgrade von ESET Endpoint Antivirus for macOS Version 6 auf Version 7 8 ........................................
5 Installation 10 ......................................................................................................................................
5 Onboarding 11 ..............................................................................................................................
5 Systemerweiterungen erlauben 12 ........................................................................................................
5 Vollständigen Datenträgerzugriff zulassen 12 ............................................................................................
5 Installation mit Kommandozeile 14 ........................................................................................................
5 Einstellungen vor der Installation 14 ......................................................................................................
5 Jamf-Einstellungen vor der Installation 17 ................................................................................................
5 Über die ESET Management-Konsole bereitstellen 20 ....................................................................................
5 Wo finde ich meine Lizenz? 20 .............................................................................................................
5 Lokale Aktivierung 21 ......................................................................................................................
5 Aktivierung mit Terminal 21 ...............................................................................................................
5 Remoteaktivierung 22 ......................................................................................................................
6 Dokumentation für remote verwaltete Endpunkte 22 ..........................................................................
6.1 Produktkonfiguration in ESET PROTECT 22 .......................................................................................
6.1 Malware Scan Engine 23 .................................................................................................................
6.1 Echtzeit-Dateischutz 24 ..................................................................................................................
6.1 Cloudbasierter Schutz 26 ................................................................................................................
6.1 Malware-Scans 27 ........................................................................................................................
6.1 ThreatSense-Parameter 28 ..............................................................................................................
6.1 Zusätzliche ThreatSense-Parameter 31 .................................................................................................
6.1 Säuberungsstufen 31 ....................................................................................................................
6.1 Update 32 .................................................................................................................................
6.1 Update-Mirror (benutzerdefinierte Updateserver) 33 ...................................................................................
6.1 Phishing-Schutz 34 .......................................................................................................................
6.1 Web-Schutz 34 ...........................................................................................................................
6.1 E-Mail-Client-Schutz 36 ..................................................................................................................
6.1 Tools 37 ...................................................................................................................................
6.1 Proxyserver 38 ...........................................................................................................................
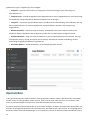
6.1 Log-Dateien 39 ...........................................................................................................................
6.1 Benutzeroberfläche 40 ...................................................................................................................
6.2 Einführung in ESET PROTECT CLOUD 41 ...........................................................................................
6.3 Einführung in ESET PROTECT 41 ......................................................................................................
6.4 Benachrichtigungen über MDM deaktivieren 43 ................................................................................
7 Arbeiten mit ESET Endpoint Antivirus for macOS 43 ............................................................................
7.1 Übersicht 44 .................................................................................................................................
7.2 Scannen 45 ..................................................................................................................................
7.2 Benutzerdefinierter Scan 48 .............................................................................................................
7.3 Sample abschicken 49 ...................................................................................................................
7.4 Schutzfunktionen 49 .....................................................................................................................
7.4 Computer 50 ..............................................................................................................................
7.4 Web und E-Mail 50 .......................................................................................................................
7.5 Update 51 ....................................................................................................................................
7.6 Tools 51 .......................................................................................................................................

7.6 Log-Dateien 51 ...........................................................................................................................
7.6 Quarantäne 52 ...........................................................................................................................
7.7 Hilfe und Support 54 .....................................................................................................................
7.7 Terminal-Hilfsprogramme und Daemons 54 ............................................................................................
7.7 Quarantäne 55 ...........................................................................................................................
7.7 Konfiguration 57 ..........................................................................................................................
7.7 Ereignisse 57 .............................................................................................................................
7.7 Erkennungsmodule im Terminal aktualisieren 58 ......................................................................................
7.7 On-Demand-Scan im Terminal 59 .......................................................................................................
8 Anwendungseinstellungen 61 ..............................................................................................................
8.1 Malware Scan Engine 62 ................................................................................................................
8.1 Leistungsausschlüsse 63 .................................................................................................................
8.1 Ereignisausschlüsse 63 ..................................................................................................................
8.1 Protokollausschlüsse 63 ..................................................................................................................
8.1 Cloudbasierte Scans 64 ..................................................................................................................
8.1 Malware-Scans 65 ........................................................................................................................
8.2 Schutzfunktionen 65 .....................................................................................................................
8.2 Engine-Empfindlichkeit 65 ...............................................................................................................
8.2 Dateischutz 66 ...........................................................................................................................
8.2 Web-Schutz 66 ...........................................................................................................................
8.2 E-Mail-Client-Schutz 67 ..................................................................................................................
8.2 Phishing-Schutz 68 .......................................................................................................................
8.3 Update 68 ....................................................................................................................................
8.3 Modul- und Produktupdates 68 ..........................................................................................................
8.4 Tools 69 .......................................................................................................................................
8.4 Taskplaner 70 ............................................................................................................................
8.4 Log-Dateien 70 ...........................................................................................................................
8.4 Proxyserver 70 ...........................................................................................................................
8.5 Benutzeroberfläche 71 ...................................................................................................................
8.5 Systemintegration 71 ....................................................................................................................
8.5 Anzuzeigende Hinweise 71 ..............................................................................................................
9 Deinstallation 71 ..................................................................................................................................
10 Technischer Support 73 .....................................................................................................................
11 Endbenutzer-Lizenzvereinbarung 74 ..................................................................................................
12 Datenschutzerklärung 81 ...................................................................................................................

1
ESET Endpoint Antivirus for macOS
ESET Endpoint Antivirus for macOS 7 ist ein neuer Ansatz für vollständig integrierte Computersicherheit. Die
neueste Version der ThreatSense Scan Engine arbeitet schnell und präzise zum Schutz Ihres Computers. Das
Ergebnis ist ein intelligentes System, das permanent vor Angriffen und bösartiger Software schützt, die Ihren
Computer gefährden können.
ESET Endpoint Antivirus for macOS 7 ist eine umfassende Sicherheitslösung und das Produkt unserer langfristigen
Bemühung, maximalen Schutz bei minimaler Systembelastung zu bieten. Mithilfe der auf künstlicher Intelligenz
basierenden Spitzentechnologien kann das Eindringen von Viren, Spyware, Trojanern, Würmern, Adware, Rootkits
und anderer durch das Internet übertragener Angriffe aktiv verhindert werden, ohne dass die Systemleistung
beeinträchtigt oder Ihr Computer vom Netz getrennt würde.
Dieses Produkt wurde speziell für die Nutzung auf Workstations in kleineren Unternehmen entwickelt. In
Verbindung mit ESET PROTECT können Sie damit eine beliebige Anzahl von Client-Workstations verwalten,
Policies und Regeln anwenden, Ereignisse überwachen und Änderungen auf beliebigen Computern im Netzwerk
verwalten.
Neuerungen in Version 7
ESET Endpoint Antivirus for macOS Version 7 ist eine neue Generation unseres Produkts, das Microservices
anstelle eines einzigen Diensts verwendet.
• Native Apple ARM-Unterstützung (ab Version 7.1.1700.0)
• Native 64-Bit-Architektur
• Verbesserte Leistung und Stabilität. Bei einem Absturz kann ESET Endpoint Antivirus for macOS
automatisch neu gestartet werden, ohne die Benutzer zu beeinträchtigen.
• Mehr Sicherheit durch Prozesse, die voneinander unabhängig sind
• Neues Hauptprogrammfenster, inklusive:
oUnterstützung für dunklen Modus
oNative Desktophinweise
oOption zur Deaktivierung der Benutzeroberfläche für Endbenutzer
• Verbesserter Echtzeit-Dateischutz
oNeueste native 64-Bit Scan Engine
oOptimiert für Multi-Core-Leistung
oEchtzeit-Scan mit lokalem Benutzer
• Brandneue native grafische Benutzeroberfläche
• Erweiterte Konfiguration von ESET LiveGrid über ESET PROTECT und ESET PROTECT CLOUD

2
• Einheitliche Kommandozeilenbefehle mit Linux-Plattform.
• Schutzstatus-Konfiguration
• Unterstützung für Leistungs- und sämtliche Ereignisausschlüsse (nach Pfad, nach Pfad und Ereignis, nach
Hash)
Vergleich zwischen den Version 6 und 7
Funktion Version 6 (aktuelle
Version)
Version 7.3 & 7.4
Architektur
Architektur Monolithisch Microservices
Architekturgestütztes Sicherheitsprofil
Hauptprozess wird unter
root ausgeführt
(Alle wichtigen
Operationen werden vom
Hauptprozess ausgeführt)
Alle Dienste werden
mit minimal
erforderlichen
Rechten ausgeführt
Reduzierter
Angriffsvektor
Schwachstellen in
einem Dienst machen
nicht die gesamte
Anwendung
angreifbar.
Wenn ein
Produktprozess
abstürzt oder
übernommen wird,
wird nicht der
gesamte Schutz
deaktiviert
Architekturgestütztes Stabilitätsprofil
Wenn der monolithische
Scanner abstürzt, fällt der
Schutz vorübergehend
aus
Automatischer
Prozessneustart bei
einem Absturz
Abstürze von nicht-
kritischen Diensten
beeinträchtigen den
Schutz nicht
Vereinfachte, für
spezifische Tasks
optimierte Dienste
Automatischer
Dienstneustart bei
einem Absturz
Unterstützung für macOS
10.12 (Sierra)
10.13 (High Sierra)
10.14 (Mojave)
10.15 (Catalina)
11 (Big Sur)
12 (Monterey)
13 (Ventura)
11 (Big Sur)
12 (Monterey)
13 (Ventura)
14 (Sonoma)
Native 64-Bit Scan Engine x x
Native 64-Bit Anwendung x x

3
Funktion Version 6 (aktuelle
Version)
Version 7.3 & 7.4
Unterstützung für mehrere Sprachen Sprachspezifisches
Installationspaket
Alle Sprachen in
einem Paket (GUI-
Sprache gleich wie
System)
Native ARM-Unterstützung ab Version 7.1.1700.0
Unterstützung für Rosetta ARM x x
Dateischutz
Erkennung potenziell unerwünschter, unsicherer und
verdächtiger Anwendungen x x
Leistungsausschlüsse x x
Ausschlüsse nach Pfad und Ereignis
Wenn Sie einen
Ereignisausschluss in ESET
PROTECT erstellen
(Dateien werden
gescannt, aber Probleme
werden ignoriert), wird
ein Leistungsausschluss
erstellt (Dateien werden
nicht gescannt).
x
Ausschlüsse nach Ereignis x
Ausschlüsse nach genauer Datei (Hash) x
Echtzeit-Dateischutz x x
Verbesserte Kompatibilität von Netzwerklaufwerken x Nicht benötigt
Mit angemeldetem Benutzer scannen x
Lokalen Laufwerke scannen x x
Wechselmedien scannen x x
Netzlaufwerke scannen x x
Beim Öffnen und Erstellen scannen x x
Beim Ausführen scannen x Ja, im Öffnen
enthalten
Prozessausschlüsse x
Cloudbasierter Schutz x x
ESET LiveGrid© Reputationssystem x x
(verlängert)
ESET LiveGrid©-Feedbacksystem x x
Differenzierte Konfiguration der gesendeten Daten x
Malware-Scans (On-Demand) x x
Symbolische Links scannen x x
E-Mail-Dateien scannen x x
Postfächer scannen x x
Archive prüfen x x
Selbstentpackende Archive scannen x x

4
Funktion Version 6 (aktuelle
Version)
Version 7.3 & 7.4
Laufzeitkomprimierte Dateien scannen x x
Alternative Datenströme (ADS) scannen x x
Smart-Optimierung aktivieren x x
Systemordner vom Scannen ausschließen x Nicht benötigt
Scannen im Hintergrund mit geringer Priorität ausführen x
Datum für „Geändert am“ beibehalten x x
Scan der Systemstartdateien x
Web und E-Mail-Schutz
Anwendungsausschlüsse x x
IP-Adressausschlüsse x x
Web-Schutz (HTTP-Scan) x x
E-Mail-Client-Schutz x x
Phishing-Schutz x x
Modulupdates
Benutzerdefinierter Proxyserver für primären/sekundären
Updateserver x x
Modulen-Rollback x x
Pre-Release-Update x x
Verzögertes Updates x x
Sonstige wichtige Funktionen
Medienkontrolle x x
Firewall
Web-Kontrolle
ERMM-Unterstützung (Kommandozeilenschnittstelle für die
Integration mit Remoteüberwachung und -verwaltung) x
Unterstützung für ESET Enterprise Inspector x x
Sonstige kleinere Funktionen
Kommandozeilenschnittstelle x
x (vereinheitlicht mit
ESET Endpoint für
Linux)
Erkennungs-Log x x
Ereignis-Log x x
Computer-Scan-Log x x
Einstellungen importieren oder exportieren x x
Quarantäne x x
Lokaler Taskplaner x x
Proxyserver-Konfiguration x x
Präsentationsmodus x x (Systemfunktion
„nicht stören“)

5
Funktion Version 6 (aktuelle
Version)
Version 7.3 & 7.4
Benutzeroberfläche
Log-Dateien x x
Erkannte Bedrohungen x x
Ereignisse x x
Computerscan x x
Medienkontrolle x x
Firewall (in Endpoint Security)
Gefilterte Websites x
Web-Kontrolle (in Endpoint Security)
Log-Filter x x
Schutzstatistiken x x
Taskplaner x x
Ausgeführte Prozesse x
Quarantäne x x
Datei zur Analyse einreichen x
Schutzstatus x x
Manuelles Modul-Update x x
Lokale Einstellungen/Konfiguration durch Benutzer x x
Einstellungen in Benutzeroberfläche importieren oder
exportieren x
Hilfe x x
Brandneue native grafische Benutzeroberfläche x
Unterstützung für dunklen Modus x
Unterstützung für Bildschirme mit hoher Auflösung x x
Funktion zum Deaktivieren der Benutzeroberfläche für
Benutzer x
Native Benachrichtigungen x
Menüleiste x x
Funktion zum Ausblenden des Menüleistensymbols x x
Integration in Kontextmenüs x
Differenzierte Kontrolle darüber, welcher Schutzstatus in der
Benutzeroberfläche angezeigt und an ESET PROTECT oder
ESET PROTECT CLOUD gemeldet wird
x x
Benachrichtigungen für System-Updates x x
Installation
Lokale Installation mit Benutzeroberfläche x x
Komponentenbasierte Installation x
Komponentenbasierte Remoteinstallation
(Komponenteninstallation benötigt zusätzliche Schritte) x

6
Funktion Version 6 (aktuelle
Version)
Version 7.3 & 7.4
Unterstützung für unbeaufsichtigte Installation (mit MDM-
Vorabgenehmigungen) x x
Produktupdate über erneute Installation x x
Produktupdate von ESET PROTECT oder ESET PROTECT
CLOUD x x
Produktaktivierung
Mit Lizenz aktivieren x x
Unterstützung für Abonnementlizenzen x x
Aktivierung über ESET PROTECT oder ESET PROTECT CLOUD x x
Aktivierung mit Offline-Lizenzdatei x
Kompatibilität mit ESET Management-Konsolen
Kompatibilität mit ESET PROTECT CLOUD x x
Kompatibilität mit ESET PROTECT x x
Einstellungen migrieren
Migrationsprozess
Ab Version 7.2 werden Ihre Einstellungen aus ESET Endpoint Antivirus for macOS Version 6 beim Upgrade
automatisch in die neue Version migriert.
Nach Abschluss der Migration wird im Startbildschirm von ESET Endpoint Antivirus for macOS eine
Benachrichtigung für die erfolgreiche Migration der Einstellungen angezeigt: Ihre Einstellungen wurden auf die
neue Version übertragen.
Policies in ESET PROTECT und ESET PROTECT CLOUD werden nicht automatisch migriert, da nicht alle
Funktionen aus Version ESET Endpoint Antivirus for macOS 6 auch in Version 7 vorhanden sind. Nach dem
Upgrade auf Version 7 müssen Sie Ihre vorhandenen Policies überprüfen und neue Policies passend zu den
in Version 7 vorhandenen Funktionen erstellen. Weitere Informationen zum Erstellen oder Löschen von
Policies finden Sie im Thema Policies:
• Policies in ESET PROTECT
• Policies in ESET PROTECT CLOUD
Policies in ESET PROTECT und ESET PROTECT CLOUD für ESET Endpoint Antivirus for macOS Version 6 und
Version 7 können gleichzeitig aktiv sein.
Falls Sie bereits ein Upgrade von ESET Endpoint Antivirus for macOS Version 6 auf Version 7 oder 7.1
durchgeführt haben, können Sie Ihre Einstellungen auch dann noch migrieren, wenn Sie auf eine spätere
Version aktualisieren. Weitere Hinweise finden Sie im Artikel zur Migration in der ESET Knowledgebase.
Alle in Version 7.X verfügbaren Einstellungen werden von Version 6 migriert, mit den folgenden Ausnahmen:
• Berechtigungseinstellungen in Version 7 nicht unterstützt)
• Benutzerdefinierter Proxyserver für Updates (benutzerdefinierter Proxy wird in Version 7 nicht
unterstützt)

7
• Quarantäne-Inhalte
• Säuberungsstufen für Scans
• Zielprofile für On-Demand-Scans
Die Einstellungen für die folgenden Funktionen werden in der .xml-Migrationsdatei gespeichert und können
geladen werden, wenn die entsprechenden Funktionen in einer zukünftigen Version von ESET Endpoint Antivirus
for macOS implementiert wurden:
• Medienkontrolle
• Logs
• Web-Schutz
• Präsentationsmodus
Sonstige Migrationsprobleme
• Benutzerdefinierte Scan-Profile werden migriert und können über ESET PROTECT, ESET PROTECT CLOUD
oder in den Programmeinstellungen verwaltet werden.
Änderungslog
Systemanforderungen
Für den optimalen Betrieb von ESET Endpoint Antivirus for macOS sollte Ihr System die folgenden Hardware- und
Softwareanforderungen erfüllen:
Systemanforderungen:
Prozessor Intel 64-bit, Apple ARM 64-Bit
Betriebssystem macOS Catalina (10.15) bis macOS Sonoma (14)
macOS Catalina Server (10.15) und höher
Arbeitsspeicher 300 MB
Freier Speicherplatz auf dem Datenträger 600 MB
ESET Endpoint Antivirus for macOS benötigt während der Installation eine funktionierende
Internetverbindung.
ESET Endpoint Antivirus for macOS Version 7.1.1700.0 und neuer bietet native Unterstützung für Apple
ARM.
Upgrade von ESET Endpoint Antivirus for macOS

8
Version 6 auf Version 7
Nach dem Upgrade von ESET Endpoint Antivirus for macOS Version 6 auf Version 7 wird ESET Endpoint
Antivirus for macOS auf die Standardeinstellungen zurückgesetzt. Inklusive der Policies in der ESET
Management-Konsole.
ESET Endpoint Antivirus for macOS Version 7 enthält zahlreiche Unterschiede zu Version 6, und einige
Funktionen wurden entfernt. Bevor Sie ESET Endpoint Antivirus for macOS aktualisieren, sollten Sie das
Thema Vergleich zwischen Version 6 und Version 7 lesen.
• Lokales Upgrade
• Upgrade über die Befehlszeile
• Upgrade über die ESET Management-Konsole
• Einstellungen migrieren
Lokales Upgrade
1. Laden Sie die neueste Installationsdatei für ESET Endpoint Antivirus for macOS herunter (.dmg).
2. Öffnen Sie die Installationsdatei (.dmg).
3. Doppelklicken Sie auf das Symbol ESET Endpoint Antivirus for macOS installieren .
4. Klicken Sie auf Weiter, falls keine andere Sicherheitsanwendung installiert ist. Wenn eine andere
Virenschutzanwendung installiert ist, kann die Installation fehlschlagen.
5. Klicken Sie auf Weiter, um die Systemanforderungen zu bestätigen.
6. Klicken Sie auf Zustimmen, um die Endbenutzer-Lizenzvereinbarung und die Datenschutzerklärung zu
akzeptieren.
7. Falls Sie den Zielordner oder den Zugriff aller Benutzer auf ESET Endpoint Antivirus for macOS ändern
möchten, klicken Sie auf Ort für die Installation ändern. Klicken Sie auf Installieren, um die Installation zu
starten.
Ort für die Installation ändern
Wählen Sie das Installationsziel aus. Wählen Sie aus, ob Sie ESET Endpoint Antivirus for macOS für alle
Benutzer des Computers oder nur für den aktuellen Benutzer installieren möchten. Sie können auch einen
bestimmten Ordner für die Installation von ESET Endpoint Antivirus for macOS auswählen. Wählen Sie die
gewünschte Option aus und klicken Sie auf Weiter, um zum Schritt Installationstyp zurückzukehren.
8. Zu Beginn der Installation werden Sie unter Umständen aufgefordert, das Administratorpasswort
einzugeben.
9. Klicken Sie auf Schließen, um die Installation abzuschließen.
10. Nach der Installation wird der Onboarding-Assistent angezeigt. Führen Sie die hier beschriebenen
Schritte aus, um Ihren Computers optimal zu schützen.

9
Upgrade über die Befehlszeile
So aktualisieren Sie ESET Endpoint Antivirus for macOS über die Befehlszeile auf Version 7:
1. Laden Sie ESET Endpoint Antivirus for macOS Version 7 herunter.
2. Verteilen Sie die .dmg-Dateien auf die Zielcomputer.
3. Führen Sie die Installation wie im Thema Installation mit Kommandozeile beschrieben aus.
ESET Endpoint Antivirus for macOS über ESET PROTECT oder ESET
PROTECT CLOUD aktualisieren
Vor dem Upgrade müssen Sie die folgenden Änderungen an den Konfigurationsprofilen in Ihrem MDM
vornehmen:
• Im Konfigurationsprofil für den vollständigen Laufwerkszugriff
Version 6 Version 7
Bezeichner com.eset.eea.6 Bezeichner com.eset.eea.g2
• Falls Sie ESET Endpoint Antivirus for macOS auf macOS 12 und höher installieren, müssen Sie den
vollständigen Laufwerkszugriff für Uninstaller.app hinzufügen. Mit dieser Option können Sie Version 6 von
Ihrem System entfernen und Version 7 in Zukunft remote deinstallieren. Fügen Sie Folgendes hinzu, um das
Konfigurationsprofil für den vollständigen Laufwerkszugriff zu konfigurieren:
ESET Endpoint Antivirus & ESET Endpoint Security auf macOS 12 Monterey
Bezeichner com.eset.app.Uninstaller
Bezeichnertyp bundleID
Codeanforderung identifier "com.eset.app.Uninstaller" and anchor apple generic and certificate
1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate
leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] =
P8DQRXPVLP
App oder Dienst SystemPolicyAllFiles
Zugriff Allow
• Im Konfigurationsprofil für den Web- und E-Mail-Schutz
Version 6 Version 7
Bezeichner des
benutzerdefinierten SSL-
VPN
com.eset.sysext.manager Bezeichner des
benutzerdefinierten SSL-
VPN
com.eset.network.manager

10
Wenn Sie vor dem Upgrade auf Version 7 die Einstellungen für Version 6 entfernen, erhalten die Benutzer
eine Benachrichtigung, dass diese Einstellungen nicht angewendet wurden. Wir empfehlen, ein neues
Konfigurationsprofil für ESET Endpoint Antivirus for macOS Version 7 zu erstellen, das Konfigurationsprofil
auf den Zielcomputern bereitzustellen, ESET Endpoint Antivirus for macOS dann zu aktualisieren und
anschließend die Konfigurationsprofile für Version 6 zu entfernen. Stellen Sie nach Möglichkeit außerdem
sicher, dass pro Gerät nur eine Installations-Policy für ESET Endpoint Antivirus for macOS existiert. Wenn
Sie sowohl ESET PROTECT als auch Jamf verwenden, stellen Sie sicher, dass jeweils nur eine Installations-
Policy existiert.
Die neuen Konfigurationsprofile für ESET Endpoint Antivirus for macOS Version 7 können Sie im Thema
Einstellungen vor der Installation herunterladen.
Nachdem Sie die neuen Konfigurationsprofile bereitgestellt haben, können Sie die Installation im Thema Über die
ESET Management-Konsole bereitstellen fortsetzen.
Installation
Installationsmethoden
Installationsmethode Installationstyp Hinweise
Installation mit der
Benutzeroberfläche
Lokal Sie können ESET Endpoint Antivirus for macOS lokal mit der .dmg-
Installationsdatei installieren. Schließen Sie vor der Installation
alle geöffneten Computerprogramme. ESET Endpoint Antivirus for
macOS enthält Komponenten, die mit anderen auf Ihrem
Computer installierten Virenschutzprogrammen in Konflikt
geraten können. Wir empfehlen daher dringend, alle anderen
Virenschutzprogramme zu entfernen, um mögliche Probleme zu
vermeiden. Nach der Installation wird der Onboarding-Assistent
angezeigt. Führen Sie die hier beschriebenen Schritte aus, um
Ihren Computers optimal zu schützen.
Installation mit
Kommandozeile
Lokal/Remote Sie können ESET Endpoint Antivirus for macOS installieren, ohne
mit der Benutzeroberfläche des Installationsprogramms zu
interagieren. Mit dieser Methode können Sie ESET Endpoint
Antivirus for macOS auch remote installieren. Wenn Sie ESET
Endpoint Antivirus for macOS remote installieren, sollten Sie die
Zustimmungseinstellungen des Benutzers vor der Installation über
MDM anzuwenden.
ESET PROTECT Remote
(Gegenstelle)
Wenn Ihr Computer in ESET PROTECT registriert ist, können Sie
einen Installations-Task erstellen, um ESET Endpoint Antivirus for
macOS auf Zielcomputern zu installieren.
ESET PROTECT CLOUD Remote
(Gegenstelle)
Wenn Ihr Computer in ESET PROTECT CLOUD registriert ist,
können Sie einen Installations-Task erstellen, um ESET Endpoint
Antivirus for macOS auf Zielcomputern zu installieren.

11
ESET Endpoint Antivirus for macOS setzt voraus, dass die Zustimmungseinstellungen des Benutzers
funktionieren. Diese Einstellungen müssen nach der Installation manuell angewendet werden. Ihr Gerät
muss in MDM registriert sein, um zu verhindern, dass die Benutzer ihre Zustimmung auf den einzelnen
Computern festlegen. Anschließend wird MDM für die Verteilung von Konfigurationsprofilen an
Zielcomputer verwendet. Wenn Sie diese Einstellungen nicht vor der Installation anwenden, erhalten die
Benutzer mehrere Popup-Hinweise, in denen sie aufgefordert werden, die Zustimmungseinstellungen
manuell anzuwenden. Wir empfehlen, vor der Installation von ESET Endpoint Antivirus for macOS
Konfigurationsprofile zu verteilen.
Onboarding
Nach der Installation von ESET Endpoint Antivirus for macOS werden Sie im Onboarding-Assistent durch die
empfohlenen und obligatorischen Schritte geführt, um den vollen Funktionsumfang von ESET Endpoint Antivirus
for macOS nutzen zu können.
1. Aktivieren Sie die empfohlenen Schutzeinstellungen, wählen Sie Ihre bevorzugten Optionen aus und klicken
Sie auf Weiter. Weitere Informationen zu ESET LiveGrid© oder potenziell unerwünschten Anwendungen
finden Sie in unserem Glossar.
2. Obligatorischer Schritt: ESET-Systemerweiterungen aktivieren. Folgen Sie den Anweisungen auf dem
Bildschirm, um mit den Einstellungen fortzufahren.
3. Obligatorischer Schritt: Proxy-Konfigurationen hinzufügen. Klicken Sie im Hinweisfenster auf Zulassen.
4. Obligatorischer Schritt: ESET Endpoint Antivirus for macOS Festplattenvollzugriff gewähren. Folgen Sie den
Anweisungen auf dem Bildschirm und erlauben Sie den Festplattenvollzugriff.
5. Als Nächstes fordert der Assistent Sie zum Aktivieren von ESET Endpoint Antivirus for macOS auf. Sie
finden mehrere Aktivierungsoptionen im Kapitel „Aktivierung“.
6. Benachrichtigungen zulassen. Wir empfehlen Ihnen, Benachrichtigungen zuzulassen, um über erkannte
Bedrohungen für Ihr System informiert zu bleiben.
Der ESET Endpoint Antivirus for macOS Onboarding-Assistent wird übersprungen.
Wenn Sie auf Später einrichten klicken, können Sie die Pflichteinstellungen überspringen. Beachten Sie
jedoch, dass der Schutz nur teilweise funktionsfähig ist.
Neustart des Onboarding-Assistenten
Öffnen Sie Finder > Anwendungen > Control-klicken (oder rechtsklicken) Sie auf das Symbol ESET Endpoint
Antivirus for macOS, wählen Sie Paketinhalt zeigen im Kurzbefehlmenü aus und öffnen Sie Contents >
Helpers > Onboarding. Sie können die obligatorischen Sicherheitseinstellungen auch manuell einrichten,
indem Sie der Anleitung im Kapitel Manuelles Onboarding folgen.
Nach der Installation von ESET Endpoint Antivirus for macOS sollten Sie Ihren Computer auf Schadcode scannen.
Klicken Sie dazu im Hauptprogrammfenster auf Scannen > Jetzt scannen. Weitere Informationen zu On-Demand-
Computer-Scans finden Sie im Abschnitt On-Demand-Computer-Scan.

12
Systemerweiterungen erlauben
Bei der Erstinstallation von ESET Endpoint Antivirus for macOS müssen Sie ESET Endpoint Antivirus for macOS die
Berechtigungen zum Schutz von Systemerweiterungen sowie den vollständigen Laufwerkszugriff erteilen.
macOS Ventura (13) und neuer
1. Öffnen Sie die Systemeinstellungen.
2. Wählen Sie Datenschutz und Sicherheit im Menü auf der linken Seite aus.
3. Blättern Sie zum Bereich Sicherheit und klicken Sie auf die Schaltfläche Details unter dem Hinweis „Einige
Systemsoftware erfordert Ihre Aufmerksamkeit, bevor sie verwendet werden kann“.
Wenn der Hinweis Einige Systemsoftware erfordert Ihre Aufmerksamkeit, bevor sie verwendet werden
kann und die Schaltfläche Details nicht angezeigt werden, wurden Systemerweiterungen bereits
zugelassen, und es sind keine weiteren Aktionen erforderlich.
4. Verwenden Sie Ihre Touch ID oder klicken Sie auf Passwort verwenden und geben Sie Ihren Benutzernamen
und Ihr Passwort ein. Klicken Sie dann auf Entsperren.
5. Aktivieren Sie sowohl den ESET Echtzeit-Dateischutz als auch den ESET Web- und E-Mail-Schutz.
6. Klicken Sie auf OK.
7. Wenn die Warnung für den ESET Web- und E-Mail-Schutz angezeigt wird und Sie aufgefordert werden, eine
Proxykonfiguration hinzuzufügen, wählen Sie Zulassen aus. Wenn Sie die Proxykonfiguration nicht zulassen,
wenn eine Warnung angezeigt wird, müssen Sie Ihren Computer neu starten, um die Warnung zu starten und die
Proxykonfiguration erneut zulassen zu können.
macOS Monterey (12) und älter
1. Öffnen Sie die Systemeinstellungen.
2. Wählen Sie Sicherheit & Datenschutz aus.
3. Klicken Sie unten links auf das Schlosssymbol, um Änderungen im Einstellungsfenster zu erlauben.
4. Verwenden Sie Ihre Touch ID oder klicken Sie auf Passwort verwenden und geben Sie Ihren Benutzernamen
und Ihr Passwort ein. Klicken Sie dann auf Entsperren.
5. Klicken Sie auf Details.
6. Wählen Sie alle ESET Endpoint Antivirus for macOS Optionen aus.
7. Klicken Sie auf OK.
Vollständigen Datenträgerzugriff zulassen
Bei der Erstinstallation von ESET Endpoint Antivirus for macOS müssen Sie ESET Endpoint Antivirus for macOS die
Berechtigungen zum Schutz von Systemerweiterungen sowie den vollständigen Laufwerkszugriff erteilen.
macOS Ventura (13) und neuer

13
1. Öffnen Sie die Systemeinstellungen.
2. Wählen Sie Datenschutz und Sicherheit im Menü auf der linken Seite aus.
3. Klicken Sie auf die Option Festplattenvollzugriff und dann auf ESET Endpoint Antivirus for macOS Ein/Aus, um
die Option zu aktivieren.
4. Verwenden Sie Ihre Touch ID oder klicken Sie auf Passwort verwenden und geben Sie Ihren Benutzernamen
und Ihr Passwort ein. Klicken Sie dann auf Entsperren.
5. Wenn eine Aufforderung zum Neustart von ESET Endpoint Antivirus for macOS angezeigt wird, klicken Sie auf
Später.
6. Klicken Sie auf ESET Echtzeit-Dateischutz Ein/Aus, um den Dateischutz zu aktivieren.
macOS Monterey (12) und älter
1. Öffnen Sie die Systemeinstellungen.
2. Navigieren Sie zur Registerkarte Datenschutz und wählen Sie im Menü auf der linken Seite die Option
Festplattenvollzugriff aus.
3. Klicken Sie unten links auf das Schlosssymbol, um Änderungen im Einstellungsfenster zu erlauben.
4. Verwenden Sie Ihre Touch ID oder klicken Sie auf Passwort verwenden und geben Sie Ihren Benutzernamen
und Ihr Passwort ein. Klicken Sie dann auf Entsperren.
5. Wählen Sie ESET Endpoint Antivirus for macOS in der Liste aus.
6. Eine Benachrichtigung über den Neustart von ESET Endpoint Antivirus for macOS wird angezeigt. Klicken Sie auf
„Später“.
7. Wählen Sie den ESET Echtzeit-Dateischutz in der Liste aus.
Wenn die Option Echtzeit-Dateischutz nicht verfügbar ist, müssen Sie zuerst Systemerweiterungen
zulassen. Führen Sie dazu die hier beschriebenen Schritte aus.
8. Klicken Sie im Warnungsdialog auf Neu starten, um ESET Endpoint Antivirus for macOS neu zu starten und die
Änderungen zu übernehmen, oder starten Sie Ihren Computer neu. Weitere Informationen finden Sie in unserem
Knowledgebase-Artikel.

14
Installation mit Kommandozeile
Überspringen Sie die Installation mit der Benutzeroberfläche, indem Sie ESET Endpoint Antivirus for macOS über
die Befehlszeile installieren. Wenn Ihr Computer nicht in MDM registriert ist, müssen Sie die
Benutzerzugriffsberechtigungen für ESET Endpoint Antivirus for macOS in den Systemeinstellungen weiterhin
manuell erteilen.
Falls Sie ESET Endpoint Antivirus for macOS remote über die Befehlszeile installieren, sollten Sie vor der
Installation von ESET Endpoint Antivirus for macOS Konfigurationsprofile mit
Benutzerzustimmungseinstellungen über MDM verteilen. Sie finden die Einstellungen für das
Konfigurationsprofil im Thema Einstellungen vor der Installation.
1. Herunterladen ESET Endpoint Antivirus for macOS.
2. Doppelklicken Sie auf die Datei oder führen Sie den folgenden Befehlszeilenprozess aus, um die
heruntergeladene .dmg-Datei einzuhängen:
a.Navigieren Sie im Terminal zum Speicherort der Datei. Geben Sie cd ~/Downloads ein.
Ersetzen Sie Downloads durch den Speicherort der heruntergeladenen Datei.
b.Geben Sie hdiutil attach eea_osx_mlp_0.dmg ein.
Ersetzen Sie eea_osx_mlp_0 durch Ihren Dateinamen.
3. Geben Sie im Terminal sudo installer -pkg /Volumes/ESET\ Endpoint\
Antivirus/.resources/Installer.pkg -target / ein.
Möglicherweise müssen Sie den Pfad zu „Installer.pkg“ durch den Pfad ersetzen, unter dem Sie die Datei
„Installer.pkg“ gespeichert haben.
4. Nach der Installation müssen Sie die Zustimmungseinstellungen des Benutzers für ESET Endpoint Antivirus
for macOS unter Manuelles Onboarding vornehmen, um sich vollständig zu schützen.
Remoteinstallation
Vor der Installation
Aufgrund der erforderlichen Rechteeinstellungen kann ESET Endpoint Antivirus for macOS nicht komplett remote
installiert werden, ohne Ihr Gerät in MDM zu registrieren. Wenn Ihr Gerät in MDM registriert ist, können Sie die
Einstellungen über Konfigurationsprofile verteilen. Wenn Ihr Gerät nicht in MDM registriert ist, müssen Sie diese
Rechteeinstellungen auf den einzelnen Computern manuell erlauben.
Falls Sie Jamf verwenden, lesen Sie auch unsere spezielle Jamf-Anleitung.
Konfigurationsprofile für ESET Endpoint Antivirus for macOS festlegen
Bevor Sie ESET Endpoint Antivirus for macOS installieren, müssen Sie die folgenden Einstellungen auf den
Zielcomputern aktivieren:
oESET-Systemerweiterungen
Wenn die ESET-Systemerweiterungen vor der Installation nicht aktiviert sind, erhalten die Benutzer
Benachrichtigungen über blockierte Systemerweiterungen, bis die ESET-Systemerweiterungen aktiviert

15
wurden.
oVollständiger Laufwerkszugriff
Wenn der vollständige Laufwerkszugriff vor der Installation nicht aktiviert ist, erhalten die Benutzer
Benachrichtigungen darüber, dass ihr Computer nur teilweise geschützt ist, bis der vollständige
Laufwerkszugriff aktiviert wurde.
oWeb und E-Mail-Schutz
Sie müssen die Konfiguration für den Web- und E-Mail-Schutz zu den Systemeinstellungen hinzufügen, um
den Web- und E-Mail-Schutz verwenden zu können.
Falls die Konfiguration für den Web- und E-Mail-Schutz nach der Installation von ESET Endpoint Antivirus for
macOS nicht vorhanden ist, erhalten die Benutzer die Meldung „ESET Endpoint Antivirus for macOS möchte
Netzwerkinhalte filtern“. Wenn die Benutzer diese Benachrichtigung erhalten, klicken Sie auf Zulassen. Wenn
Sie auf Nicht erlauben klicken, funktioniert der Web- und E-Mail-Schutz nicht.
Um die genannten ESET-Einstellungen remote zu aktivieren, muss Ihr Computer bei einem MDM-Server (Mobile
Device Management) registriert sein, beispielsweise Jamf.
ESET-Systemerweiterungen aktivieren
Führen Sie eine der folgenden Aktionen vor der Installation aus, um Systemerweiterungen auf Ihrem Gerät
remote zu aktivieren:
oLaden Sie die .plist-Nutzlast herunter. Erstellen Sie ein Konfigurationsprofil in Ihrem MDM mit der .plist-
Nutzlast.
oErstellen Sie ein Konfigurationsprofil in Ihrem MDM mit den folgenden Einstellungen:
Teambezeichner (TeamID) P8DQRXPVLP
Paketbezeichner (BundleID) com.eset.endpoint
com.eset.network
Vollständigen Laufwerkszugriff aktivieren
Führen Sie eine der folgenden Aktionen vor der Installation aus, um den vollständigen Laufwerkszugriff remote zu
aktivieren:
oLaden Sie die .plist-Nutzlastdatei für ESET Endpoint Antivirus for macOS herunter.Erstellen Sie ein
Konfigurationsprofil in Ihrem MDM mit der .plist-Nutzlast.
Falls Ihr Gerät mit ESET PROTECT oder ESET PROTECT CLOUD verwaltet wird, müssen Sie den vollständigen
Laufwerkszugriff auch für den ESET Management Agent aktivieren. Laden Sie die .plist-Nutzlastdatei für ESET
Management Agent herunter.
oErstellen Sie ein Konfigurationsprofil mit den folgenden Einstellungen:
ESET Endpoint Antivirus
Bezeichner com.eset.eea.g2
Bezeichnertyp bundleID
Codeanforderung identifier "com.eset.eea.g2" and anchor apple generic and
certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = P8DQRXPVLP

16
App oder Dienst SystemPolicyAllFiles
Zugriff Allow
Bezeichner com.eset.endpoint
Bezeichnertyp bundleID
Codeanforderung identifier "com.eset.endpoint" and anchor apple generic and
certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = P8DQRXPVLP
App oder Dienst SystemPolicyAllFiles
Zugriff Allow
Auf macOS 12 Monterey und höher
Bezeichner com.eset.app.Uninstaller
Bezeichnertyp bundleID
Codeanforderung identifier "com.eset.app.Uninstaller" and anchor apple generic and
certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and
certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and
certificate leaf[subject.OU] = P8DQRXPVLP
App oder Dienst SystemPolicyAllFiles
Zugriff Allow
ESET Management Agent
Bezeichner com.eset.remoteadministrator.agent
Bezeichnertyp bundleID
Codeanforderung identifier "com.eset.remoteadministrator.agent" and anchor apple
generic and certificate 1[field.1.2.840.113635.100.6.2.6] /*
exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /*
exists */ and certificate leaf[subject.OU] = P8DQRXPVLP
App oder Dienst SystemPolicyAllFiles
Zugriff Allow
Nachdem Sie den vollständigen Laufwerkszugriff und die Systemerweiterungen remote erlaubt haben,
werden diese Einstellungen unter Systemeinstellungen > Datenschutz und Sicherheit möglicherweise als
deaktiviert angezeigt. Wenn ESET Endpoint Antivirus for macOS keine Warnungen anzeigt, sind der
vollständige Laufwerkszugriff und die Systemerweiterungen erlaubt, unabhängig von dem unter
Systemeinstellungen > Datenschutz und Sicherheit angezeigten Status.
Web und E-Mail-Schutz
Führen Sie vor der Installation eine der folgenden Aktionen aus, um die Konfiguration für den Web- und E-Mail-
Schutz remote zu den Systemeinstellungen hinzuzufügen:
oLaden Sie die .plist-Nutzlastdatei herunter. Erstellen Sie ein Konfigurationsprofil in Ihrem MDM mit der
.plist-Nutzlast. Ihr Computer muss im MDM-Server registriert sein, um Konfigurationsprofile auf diesen
Computern bereitstellen zu können.
oUm ein Konfigurationsprofil zu erstellen, erstellen Sie ein VPN-Konfigurationsprofil mit den folgenden
Einstellungen:
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
Seite laden ...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
ESET Endpoint Antivirus for macOS 7 Bedienungsanleitung
- Typ
- Bedienungsanleitung
Verwandte Papiere
-
ESET Smart TV Security 3 Bedienungsanleitung
-
ESET Endpoint Antivirus for macOS 6.10 Bedienungsanleitung
-
ESET Endpoint Security for macOS 6.1X Bedienungsanleitung
-
ESET Endpoint Antivirus for macOS Benutzerhandbuch
-
ESET PROTECT Cloud Bedienungsanleitung
-
ESET Endpoint Security for macOS 6.9 Bedienungsanleitung
-
ESET PROTECT Cloud Bedienungsanleitung
-
ESET PROTECT 8.0—Guide Bedienungsanleitung
-
ESET Endpoint Antivirus for Windows 10 Bedienungsanleitung
-
ESET PROTECT 8.0—Installation/Upgrade Guide Installation/Upgrade Guide























































































